Strategies for Signals Intelligence from Antennas to Analysis
Overview
Contents
- Goals of Signals Intelligence
- Strategies for Analyzing Jamming Signals
- FFT-Based Signal Analysis
- Joint Time-Frequency Analysis (JTFA)
- “Packet Sniffing” on an Interference Signal
Introduction
In many scenarios, the traditional approach to signals intelligence using benchtop vector signal analyzers and spectrum analyzers is insufficient because of the limited acquisition sizes of these instruments. However, with recent innovations in the PC industry such as the PCI Express bus and improved hard drive disk speeds, you can use PXI instruments in RF stream-to-disk systems with off-the-shelf instrumentation. In fact, today’s PXI-based RF stream-to-disk solutions enable the recording of time-continuous RF bandwidth at frequencies up to 26.5 GHz. Typically, a 2 TB RAID (redundant array of independent disks) system helps you stream up to 20 MHz of RF bandwidth to disk for five hours or more. This paper does not discuss RF stream-to-disk system technologies, but you can learn more about them with these RF record and playback resources
Goals of Signals Intelligence
This paper examines two types of interference signals and the analysis techniques typically used to identify them. These two types of interference signals are “jamming” signals that obstruct communication channels and pirating signals that attempt to use the existing communications infrastructure in an unauthorized manner. Both are considered interference signals, but the motivation behind each type of signal, as well as the analysis techniques used to characterize them, are different.
Strategies for Analyzing Jamming Signals
Particularly in military scenarios, it is often necessary to identify interference from systems attempting to obstruct a communications channel. Frequently called “jamming” signals, this type of interference signal is able to jam a communications signal by producing unwanted power within the band of interest. Moreover, there are various types of signals that are commonly used as jamming signals. Common types of jamming signals include single tones, random white noise, pulsed signals, frequency hopping signals, and modulated “fake” communications signals. Each of these produces trade-offs between effectiveness, power requirements, ease of generation, and difficulty of detection. For example, the generation of a single carrier in an existing communications channel is relatively simple, but a single carrier is often ineffective and is easy to detect. On the other hand, the generation of broadband white noise can be extremely effective at obstructing a communications link. But this method results in significant power requirements and is easy to detect if the signal is not periodic.
Some of the more interesting types of jamming signals are pulsed or frequency hopping signals. These types of jamming signals are generally effective and can be difficult to detect using a traditional spectrum analyzer. The difficulty lies in the need to capture both time and frequency information regarding the signal of interest. As a result, PXI stream-to-disk systems are commonly used as a method to capture a dedicated portion of RF bandwidth for several hours of time. Once you have recorded the bandwidth, you can typically use one of two methods to analyze the power, frequency, and timing characteristics of jamming signals: fast Fourier transform (FFT)-based analysis and joint time-frequency analysis (JTFA).
FFT-Based Signal Analysis
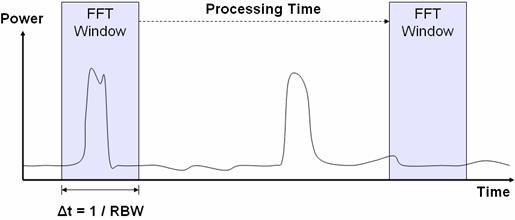
When performing FFT-based analysis of a jamming signal, you can use two processing methods: inline and postprocessing. While inline processing provides immediate results, postprocessing can offer the richest set of data. To illustrate this, see the Figure 1 graph for a pulsed jamming signal.
Figure 1. Power versus Time of a Pulsed Jamming Signal
As Figure 1 illustrates, the identification of subsequent jamming pulses is difficult in the absence of continuous acquisition. The solution to this challenge is to record the RF data for a period of time and analyze it after the acquisition is complete.
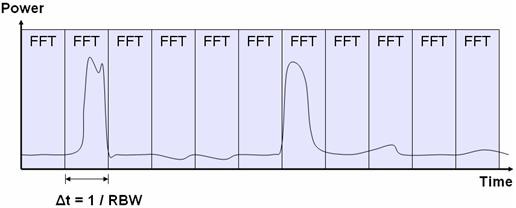
In this scenario, a chunk of RF spectrum is acquired over a long period of time and then analyzed in blocks. Using this technique, you can customize the FFT size to match the duration of the pulse itself. This is illustrated Figure 2.
Figure 2. Postprocessing Using FFT Analysis
As Figure 2 shows, by postprocessing the data, you can use an FFT size that you can customize according to the duration of the jamming pulse. This technique provides the most accurate method of characterizing pulse amplitude because it reduces the effect of the power being spread out over time.
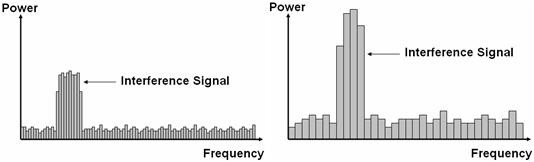
Because the resolution bandwidth (RBW) determines the acquisition time of the signal, it can affect the displayed power level of a transient signal. The amplitude of the burst might last as briefly as a few microseconds, so its power is being spread out over time in a long acquisition. Thus, you can more accurately characterize the frequency and amplitude of an interference signal using a short acquisition window. This is illustrated in Figure 3.
Figure 3. Power versus Frequency for Small versus Large RBW
Figure 3 shows the two FFTs of the jamming burst. However, the first graph depicts the use of a larger acquisition window. A longer acquisition time reduces the RBW of the measurement, but it also reduces the amplitude of the jamming pulse.
As seen from this example, the ability to customize an FFT size is one benefit of performing postanalysis on a continuous RF signal. Using this technique, you can match the FFT window exactly with the timing of the pulse for a more accurate view of the frequency domain.
Joint Time-Frequency Analysis (JTFA)
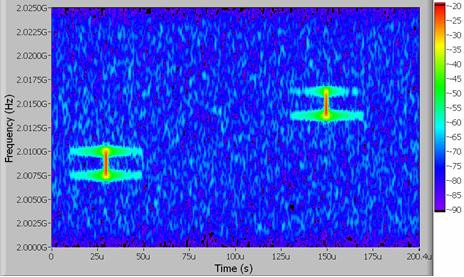
A second technique used to capture both the time and frequency information of interference signals is JTFA with a spectrogram. Similar to the FFT-based approach shown above, the spectrogram works by performing an FFT on subsequent time-domain chunks of data. You can reconstruct the resulting processed data as a 3D plot. For example, see how the data from a spectrogram is illustrated on a 3D waterfall graph in Figure 4.
Figure 4. JTFA Using the 3D Spectrogram
As Figure 4 shows, you can use a spectrogram to visualize a much richer set of data by displaying both power and frequency over time. In this figure, you can see that the jamming signal lasts for only a small period of time (approximately 25 µs). In addition, you can see that the spectrogram transitions in frequency as well. In this case, it moves from a center frequency of 2.009 GHz to 2.016 GHz. Note that the timing information shown above is not available on a traditional spectrum analyzer because it captures only power versus frequency. Moreover, only a stream-to-disk-based solution enables a vector signal generator to capture timing information over a long period of time.
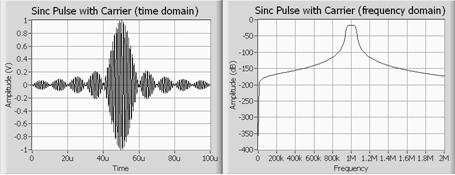
One interesting characteristic of the jamming signal above is that it contains a nearly constant power over a small frequency bandwidth. With this characteristic, you can identify the interference as a sinc pulse that has been multiplied by a carrier. For reference, the time and frequency domains of this type of signal are illustrated in Figure 5.
Figure 5. Time and Frequency Domains of Sinc Pulse with Carrier
In the figure 4 and 5 spectrogram view, a sinc pulse is traditionally difficult to detect because it is fundamentally periodic in nature. However, conducting the JTFA of this signal using a spectrogram provides the necessary timing information to identify characteristics such as time between pulses, pulse bandwidth, and pulse amplitude.
“Packet Sniffing” on an Interference Signal
A second type of interference is a pirating or piggybacking communication signal. In this application, the interferer attempts to use the existing telecommunications infrastructure to transmit an illegal communications channel. For example, an illegal transmitter attempts to use a repeater tower to rebroadcast his custom communications channel. Because the repeater simply amplifies a specified band of spectrum, the interferer can use it to amplify his signal as well as the intended signals.
Again, you can accomplish the packet sniffing of a given signal by recording a specified bandwidth and storing it to disk. Once captured, this data can be postprocessed with a variety of methods. Just as with the analysis of jamming signals, you can perform postanalysis such as FFT and JTFA to identify frequency, power, and amplitude information about the interference signal. However, for packet sniffing applications, you can demodulate the baseband waveform as well. This is illustrated in Figure 6.
Figure 6. Analysis of Baseband Waveforms Using the NI LabVIEW Modulation Toolkit
Figure 6 shows how you can analyze baseband waveforms that have been stored on hard disk using one of many demodulation subroutines in NI LabVIEW software. The figure depicts the icons for the PSK, QAM, and FSK demodulation routines from the LabVIEW Modulation Toolkit. However, note that the toolkit also offers routines for ASK, FM, AM, PM, CPM, MSK, and custom demodulation. The demodulation of an unknown carrier is not trivial. To accurately return the bitstream of a digitally modulated carrier, it is important to know the symbol rate of the carrier. You can estimate this by observing the channel width, but you often must determine the symbol rate experimentally by using the symbol rates of known communications standards.
By demodulating the communications signal of an interference signal, you can analyze the individual bitstream being transmitted over the communications channel. In some cases, you can decode this information by matching it with known preamble information. Typically, the greatest challenge occurs in decoding meaningful information from a bitstream of data.
Conclusion and Resources
As signals intelligence applications require you to detect and analyze more sophisticated types of interference signals, the instrumentation requirements increase as well. This paper has shown how you can use stream-to-disk systems with a vector signal analyzer to capture a much richer set of data for postanalysis. As a result, you can take advantage of analysis routines such as custom FFTs, joint-time frequency spectrograms, and demodulation using a variety of modulation schemes. For more information on PXI RF stream-to-disk solutions, refer to the following resources:
- White paper: From RF to RAID: Enabling Technologies of RF Stream-to-Disk Systems
- Modular Instruments for PXI Express