SELinux – Addressing Access Control Security in LabVIEW RIO Devices
Contents
The premise of the Industrial Internet of Things (IIoT) is to create a network of physical objects, systems, platforms and applications containing embedded technology that can communicate and share information with each other. This vast network of industrial connected systems uses data analytics to improve industrial performance and solve problems by making machines smarter through local processes and communications. However, this approach also comes with a set of challenges from a security point of view.
LabVIEW RIO devices such as the CompactRIO system include a range of security features to protect applications in the IIoT. For a comprehensive list of security measures in LabVIEW RIO devices please read Best Practices for Security on RIO Systems. Security-Enhanced Linux (SELinux) expands the list of security features by making possible to add access control security policies on NI Linux Real-Time – based devices. This document provides an introduction to SELinux management as well as resources for advanced configuration.
What is SELinux?
SELinux was originally created to provide a mechanism to confine the damage caused by malicious applications by enforcing the separation of information based on confidentiality and integrity requirements. SELinux is a Linux kernel security module that provides mechanisms to support mandatory access control (MAC) security policies. Its goal is to separate enforcement of security decisions from the security policy itself by providing flexible mandatory access control (MAC) directly in the operating system.
SELinux defines the access and transition rights of users, applications, processes, and files on the system. These interactions are governed by the security policy to protect the system from malicious applications that could potentially harm or destroy the system. When an application attempts to access a file or resource, if that access would be permitted by the traditional Unix permissions, SELinux performs an additional check against the security context defined by the installed policy to decide whether to allow or deny access to that resource.
What is the SELinux Policy?
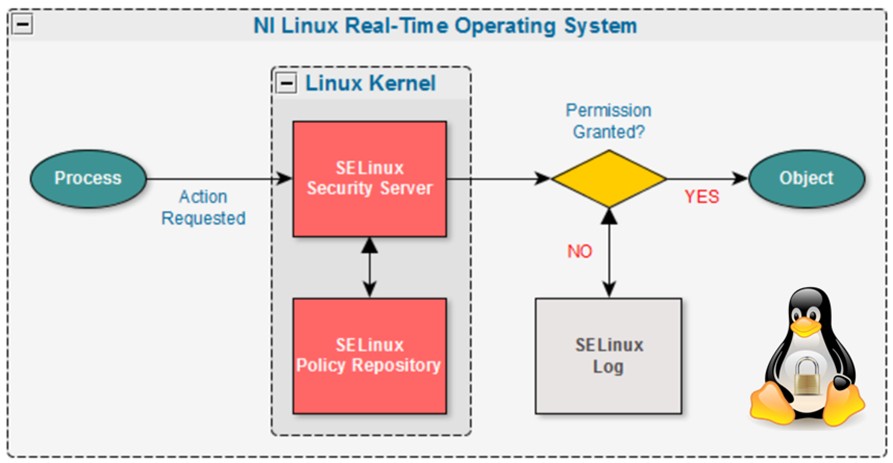
The SELinux policy contains the set of rules that govern the interactions between processes and objects. Every process has a label and similarly every object has a label associated to it. This is also truth for ports, devices, and even hostnames. This way, SELinux is a labeling system that uses policies containing rules to control the access of a process label to an object label like a file. The kernel is responsible for enforcing these rules and this action is known as Mandatory Access Control (MAC).
Figure 1. Security-Enhanced Linux Decision Process
The SELinux primary model of enforcement is called type enforcement. This means, that the definition of the label of a process is based on its type. Similarly, the label of an object such as a file is based on its type. For example, the objects in the home directory could be labeled as user_home_t. This represents the type, and in this case this means that the policy should treat all the objects with that label as home directory files. This is also the case for processes, for example a web browser could be running as webbrowser_t. Based on these labels, type enforcement allows you to specify what application label can access what resource label. For instance, the instruction allow webbrowser_t user_home_t : file { read write }; allows the web browser process running as webbrowser_t to read and write files in the home directory, labeled as user_home_t. This way, SELinux isolates objects and processes based on its type by denying access to processes not considered in the definition of the policy.
NI Linux Real-Time targets include a default reference policy containing a set of standard rules. This policy only restricts access to a few widely exposed services. Thus, user sessions are not restricted and legitimate user operations will be allowed. However, this does not enhance the security of services running on the embedded hardware target. Since most applications differ in terms of security needs, custom policies can be defined in SELinux to serve such purposes. We recommend users unfamiliar with this tool to work directly with third party SELinux integrators to define tailored policies for specific applications.
SELinux Operating Modes
SELinux has 2 main modes of operation: Enforcing and Permissive. In normal operation, an SELinux hardened system will run with SELinux in enforcing mode. This means that the SELinux policy is in effect and accesses that it does not explicitly permit will be denied. However, for testing and debugging purposes, SELinux can also be switched to permissive mode.
The permissive mode allows a system to run with SELinux enabled, while still allowing all the accesses that would otherwise be denied by the running policy. This means that a system running in permissive mode is not protected by SELinux. The purpose is to log what SElinux would have denied, allowing the administrator an insight into what would happen with SELinux in enforcing mode. This is useful when creating a new policy or debugging unexpected denials with an existing policy.
Enforcing – The SELinux security policy is enforced
Permissive- The SElinux security policy is not enforced but SELinux still prints warnings for debugging and troubleshooting purposes
Resources
To learn more about how to configure and use SELinux, please read the following resources:
The registered trademark Linux® is used pursuant to a sublicense from LMI, the exclusive licensee of Linus Torvalds, owner of the mark on a worldwide basis. Permission to use and/or modify the penguin image is granted by Larry Ewing and The GIMP.